Dest0g3 520 迎新赛部分pwn题复现
ez_aarch
aarch64架构的ret2text,除了canary全开了
运行程序
1 | qemu-aarch64 -L /usr/aarch64-linux-gnu/ ./stack |
用gdb-multiarch调试确定溢出长度
先将程序在指定端口跑起来
1 | qemu-aarch64 -g 1234 -L /usr/aarch64-linux-gnu/ ./stack |
gdb-multiarch调试
1 | gdb-multiarch ./stack |
按c继续运行程序,用pwntools生成字符串并输入到qemu运行的程序中
1 | from pwn import * |
此时再回到gdb
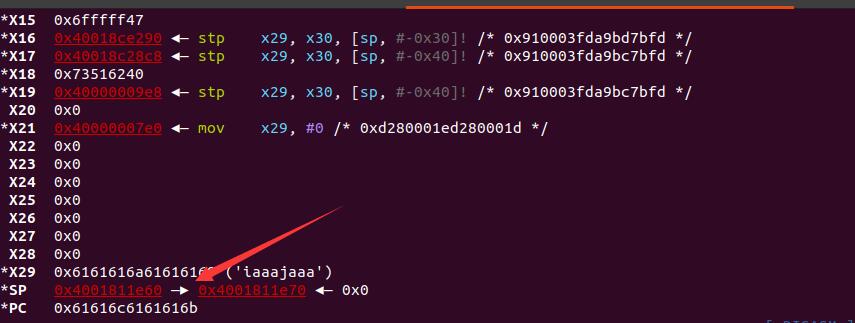
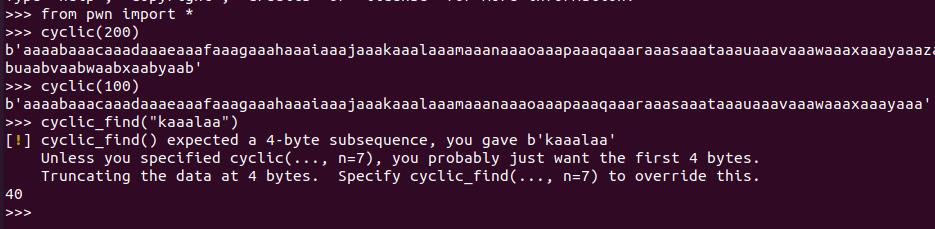
可以看到PC寄存器已经改成了kaaalaa,用pwntools确定偏移
1 | cyclic_find("kaaalaa") |
得到偏移为40
exp
1 | from pwn import * |
ez_pwn
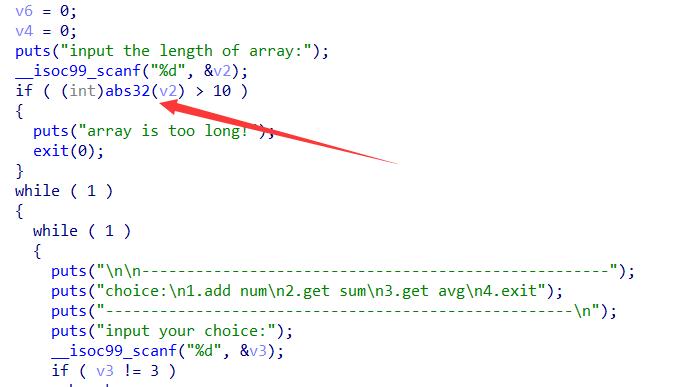
32位数组溢出
这里输入数组长度的时候用了abs取绝对值,所以可以-1得到一个很大的值
数组溢出可以参考这篇:数组溢出
然后gdb调试得到表示数组下标的地方,改成到返回地址的偏移然后和正常的rop一样泄露libc,getshell一样的操作覆盖返回地址和传参就行
需要注意的是输入数组用的是%d,最大值为0xffffffff,所以最后输入system或者one_gadget的时候要输入负数
exp
1 | from pwn import * |
dest_love
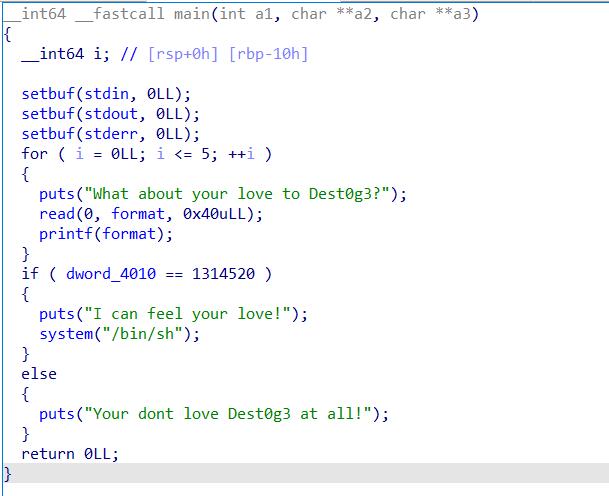
格式化字符串漏洞,让dword_4010==1314520就可以getshell,但是这个值不在栈上,所以就之间格式化字符串改返回地址为one_gadget了
exp
1 | from pwn import * |
ezuaf
题目是很常见的菜单题,漏洞也很明显,就是一个uaf,这里主要是学习了一下glibc-2.33新引进的防护进制:safe-linking
1 | /* Safe-Linking: |
整体的一个加密方式就是
1 | p->fd = ((&p->fd)>>12) ^ REVEAL_PTR(p->fd) |
当前堆块的fd会等于当前堆块地址 >> 12 ^ 原fd(相邻先被释放的堆块地址)
创建两个堆块然后free进tcache 中
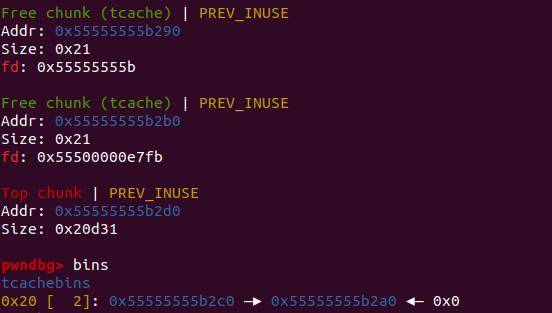
接下来按上面的公式来算一下
第一个被释放的堆块
1 | fd = (0x55555555b2a0 >> 12) ^ 0 |
第二个被释放的堆块
1 | fd = (0x55555555b2c0 >> 12) ^ 0x55555555b2a0 |
这里可以直接理解为新的fd为当前堆的data区域的地址异或上一个key,而这个key即是第一个free进tcachebins中的堆块的data区域地址>>12得到
所以2.33版本以上的uaf只是比平常的攻击多了个异或key的过程,key的值可以通过泄露第一个free的堆块的fd来得到
exp
1 | from pwn import * |